Configuring Admin Access with TACACS+ as an External Source
Intro
RADKit administrators can be configured locally on RADKit, or can be authenticated by a TACACS+ server.
At the login screen, the RADKit Service will query the TACACS+ server to verify if the entered user ID and password are permitted to connect as a RADKit administrator.
If the TACACS+ responds ACCESS_ACCEPT, the user will be let in.
Setup a TACACS+ External Source on RADKit
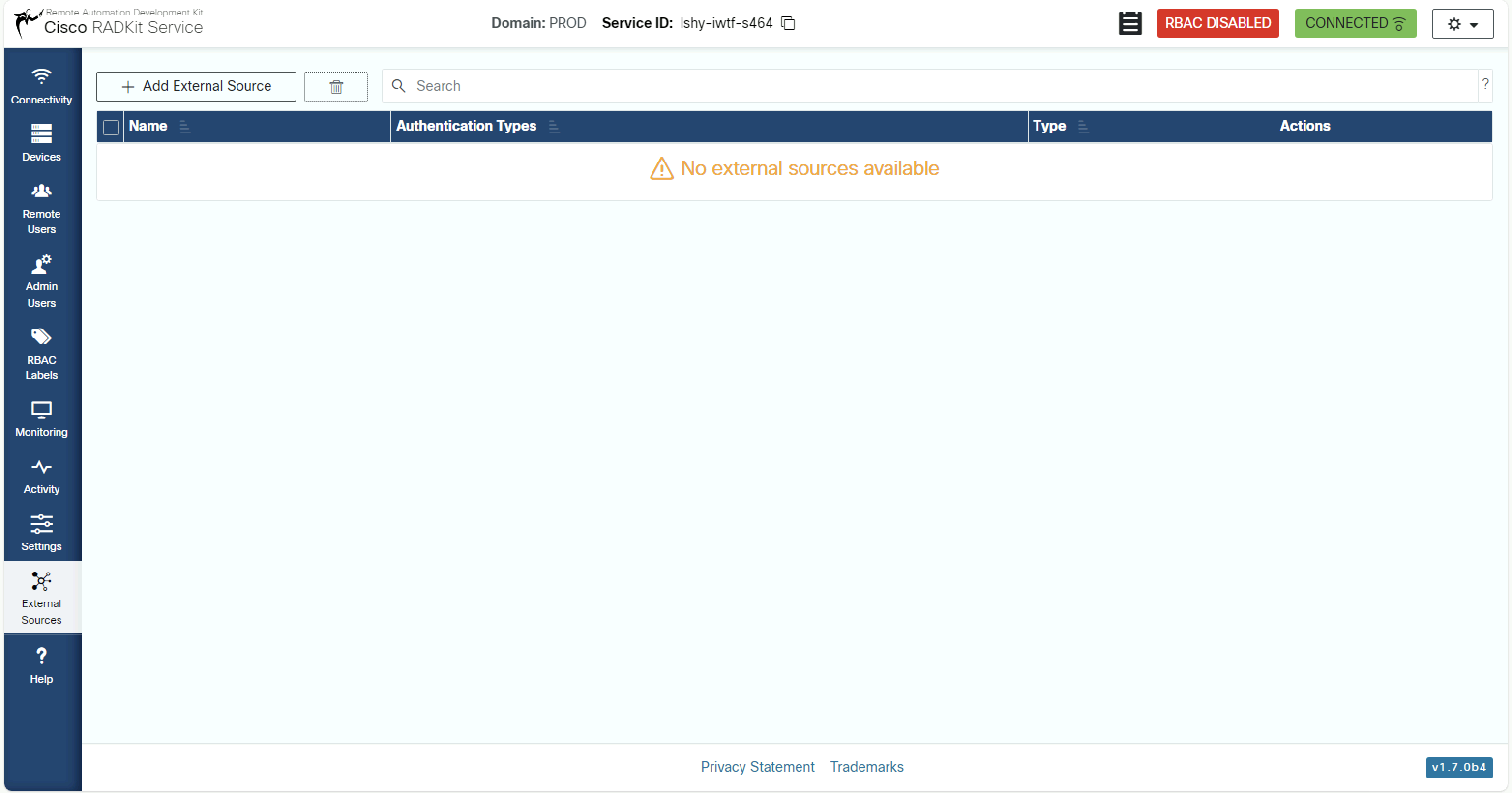
Navigate to External Sources. If none are configured, you will be greeted with he following screen:
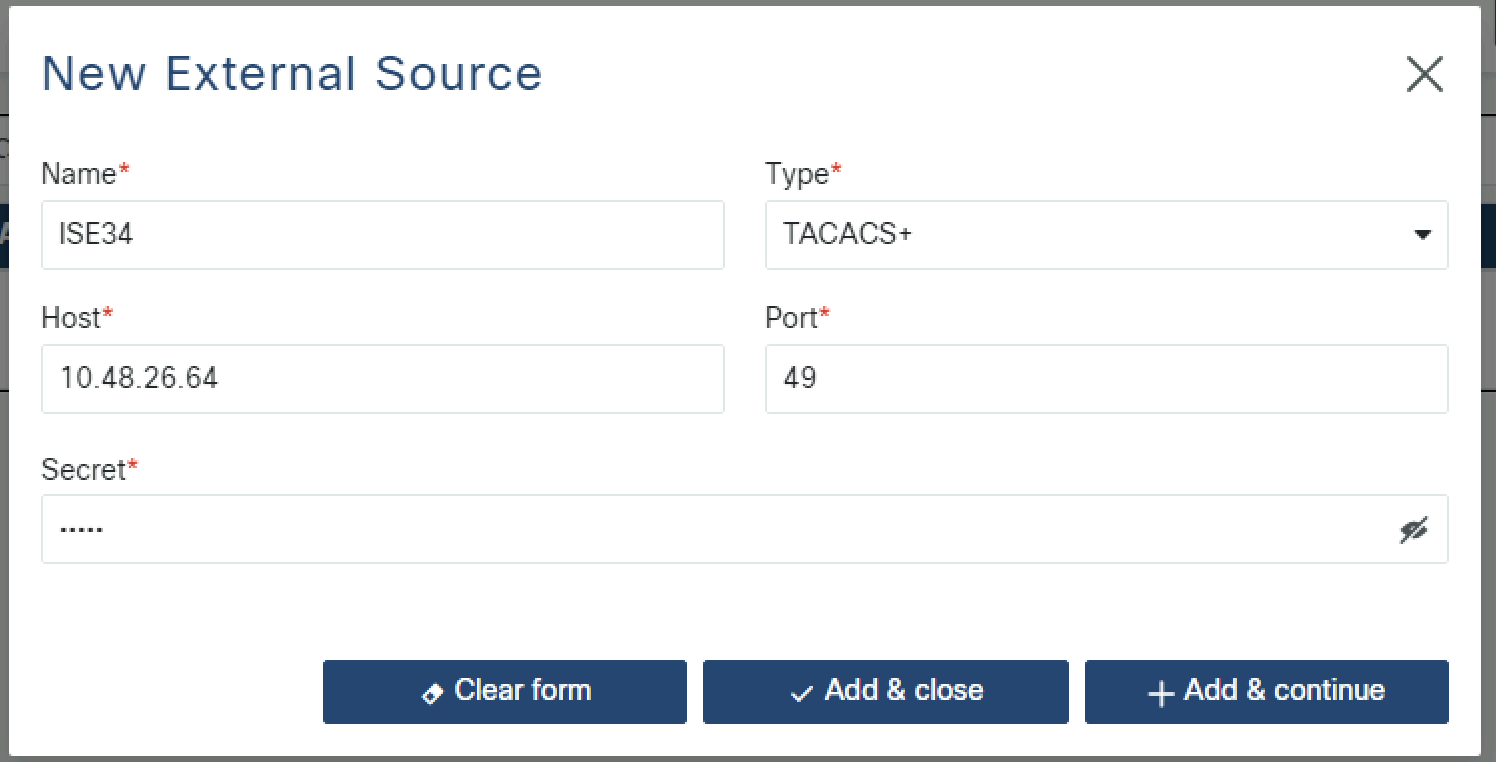
Click Add External Source. A dialog box opens.; configure the necessary information:
Name: the source name (e.g. ISE34) is a user-chosen name that represents the TACACS+ server in RADKit
Type: select
TACACS+from the drop downHost: the ip address or host name of TACACS+ Server
Port: the TACACS+ port number (49 is default TACACS+ port)
Secrete: the shared secret that matches the secret configured on your TACAC+ server (an ISE example will be given later).
When complete, click Add & close.
You now have completed the set up of the TACACS+ server in RADKit.
Setup an Identity Service Engine (ISE) for TACACS+
Declare RADKit as a Network Device
A Network Device needs to be declared on ISE to authorize RADKit Service to place TACACS+ requests.
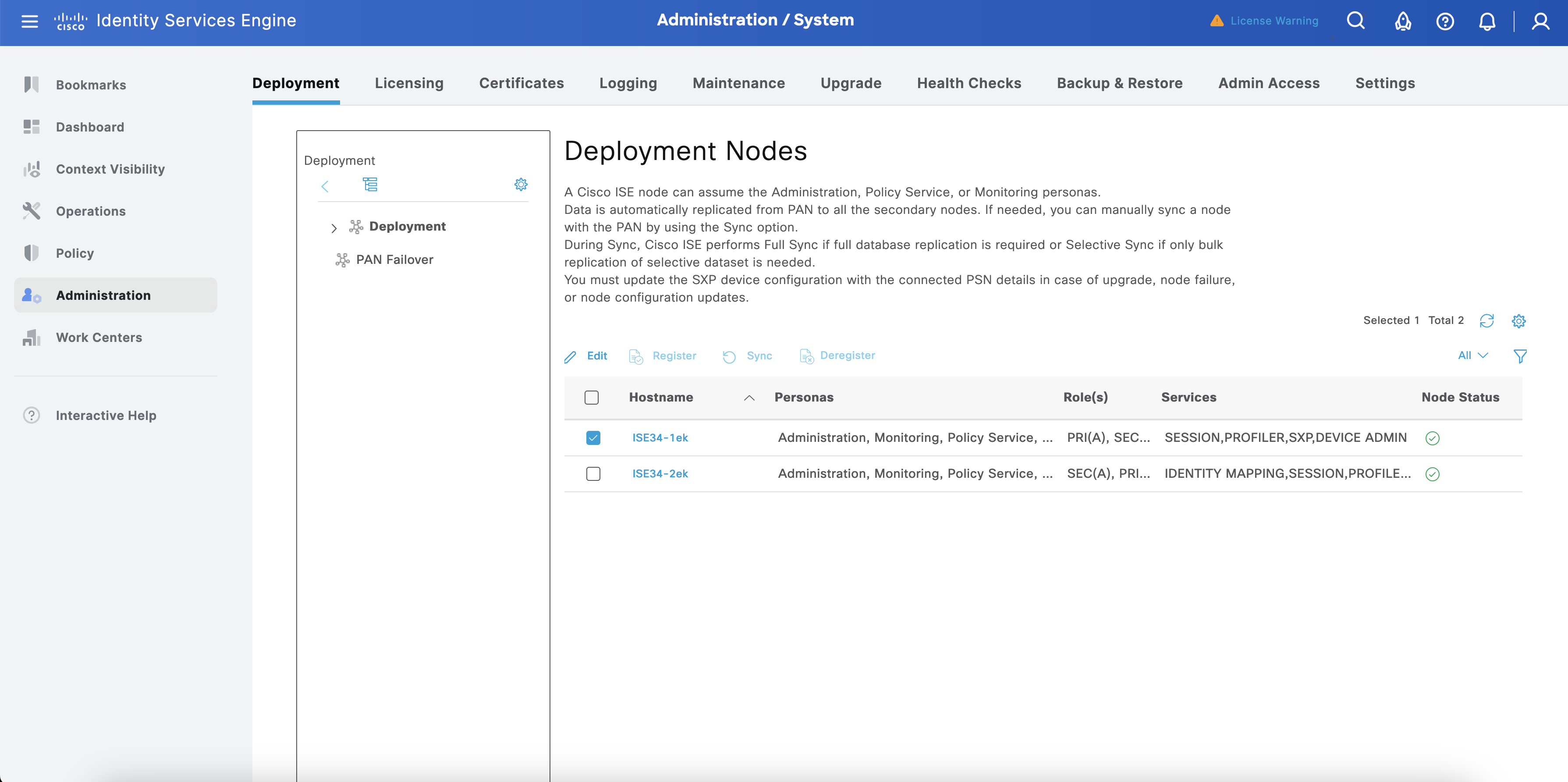
On ISE, Navigate to Administration > System > Deployment. Select ISE server and click Edit.
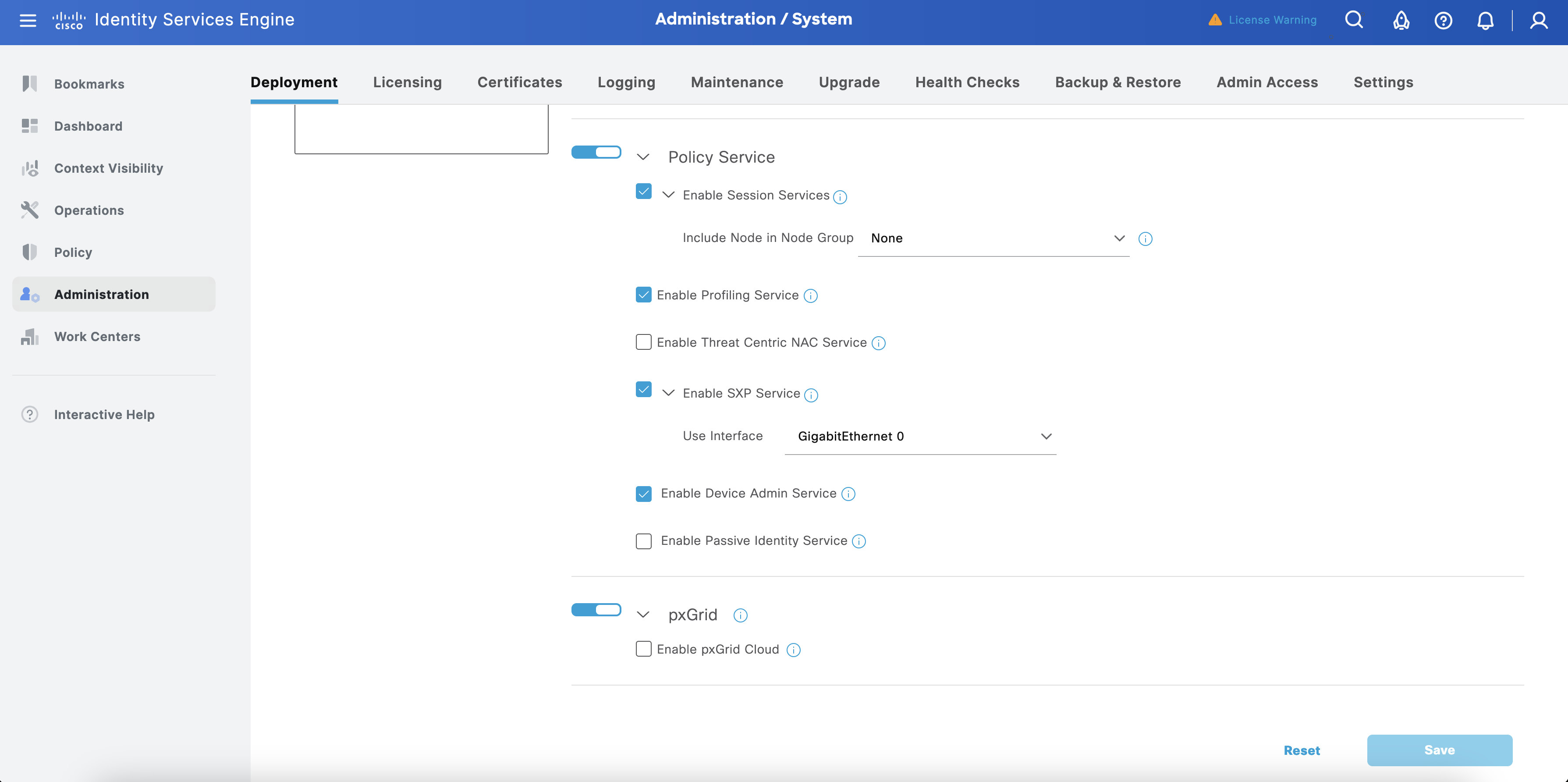
Enable Device Admin Service and click Save.
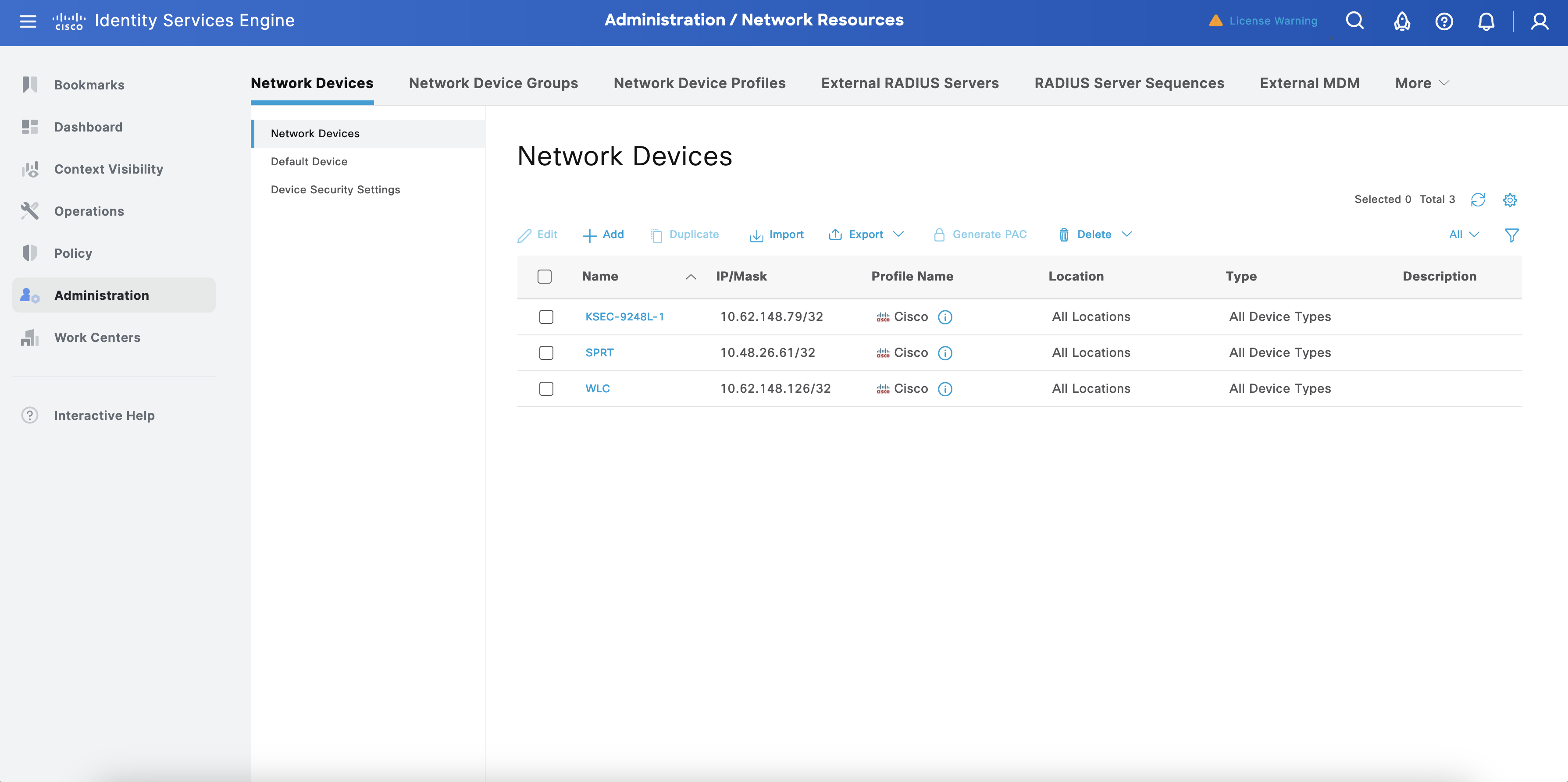
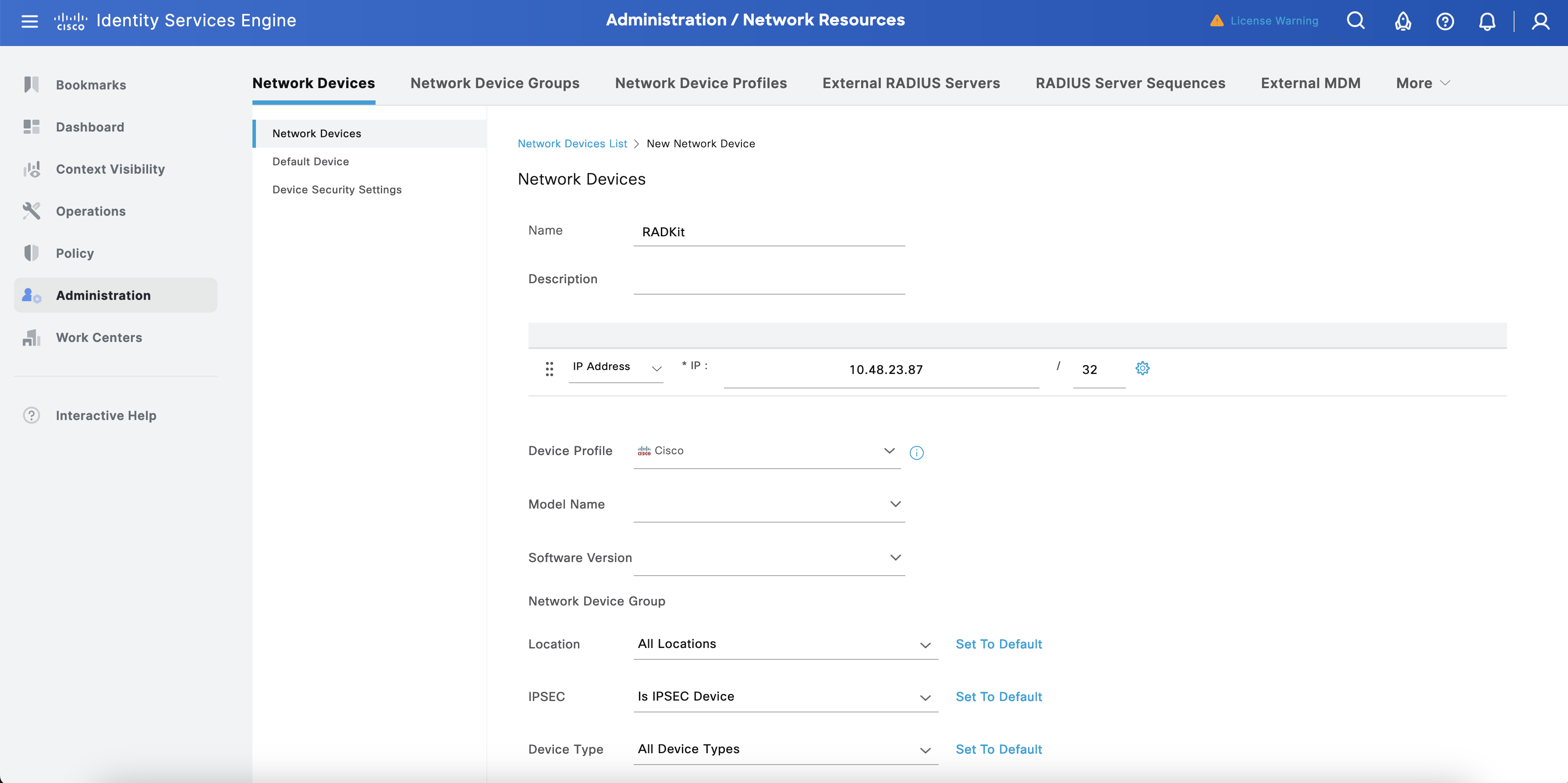
Now add the RADKit as an ISE Network Device. Navigate to Administration > Network Resources > Network Device.
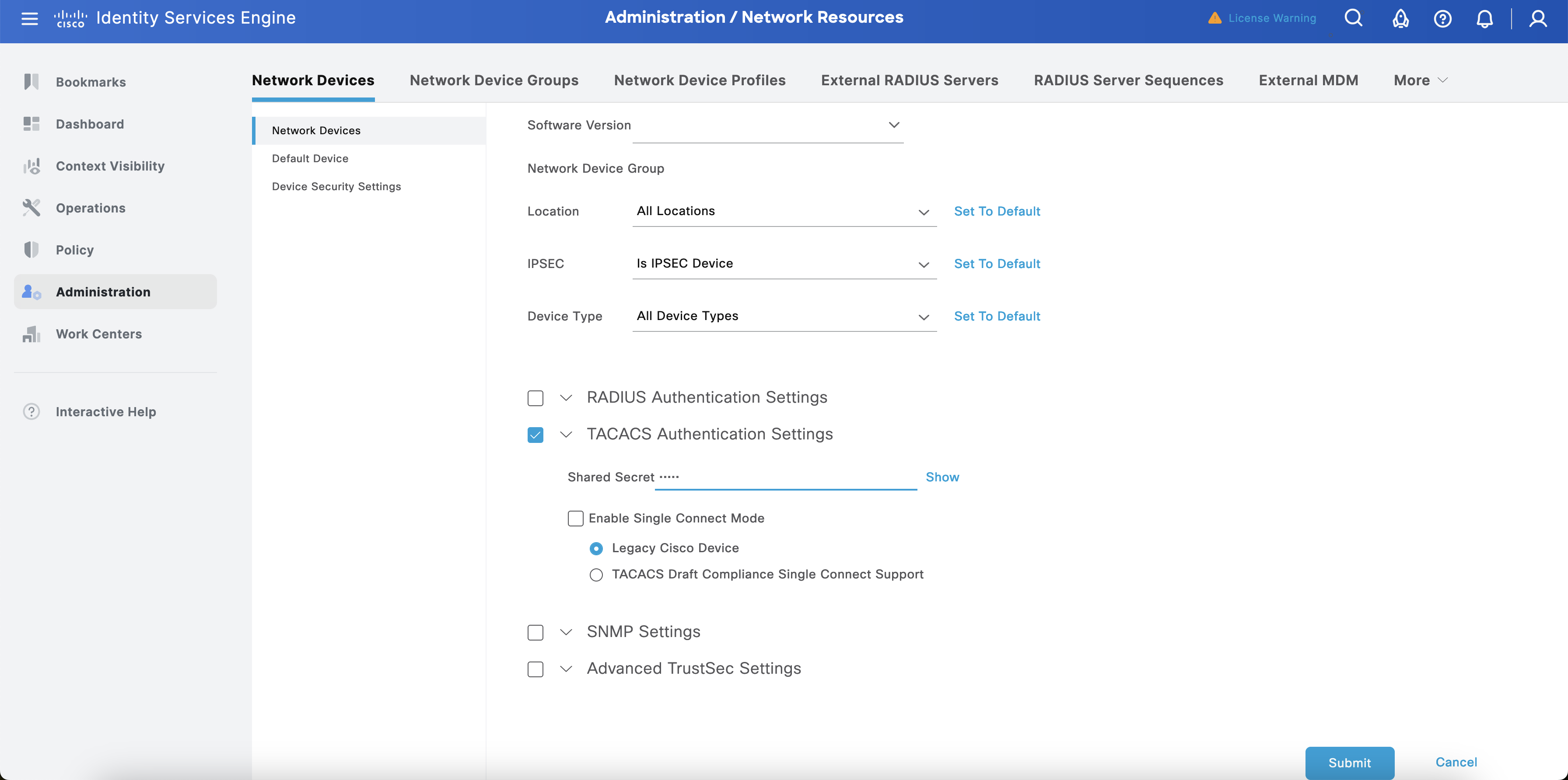
Select + Add. In the new screen, configure the Name, IP (IP address of RADKit) and TACACS+ Shared Secret. Select Save
Create a RADKit admin user on ISE
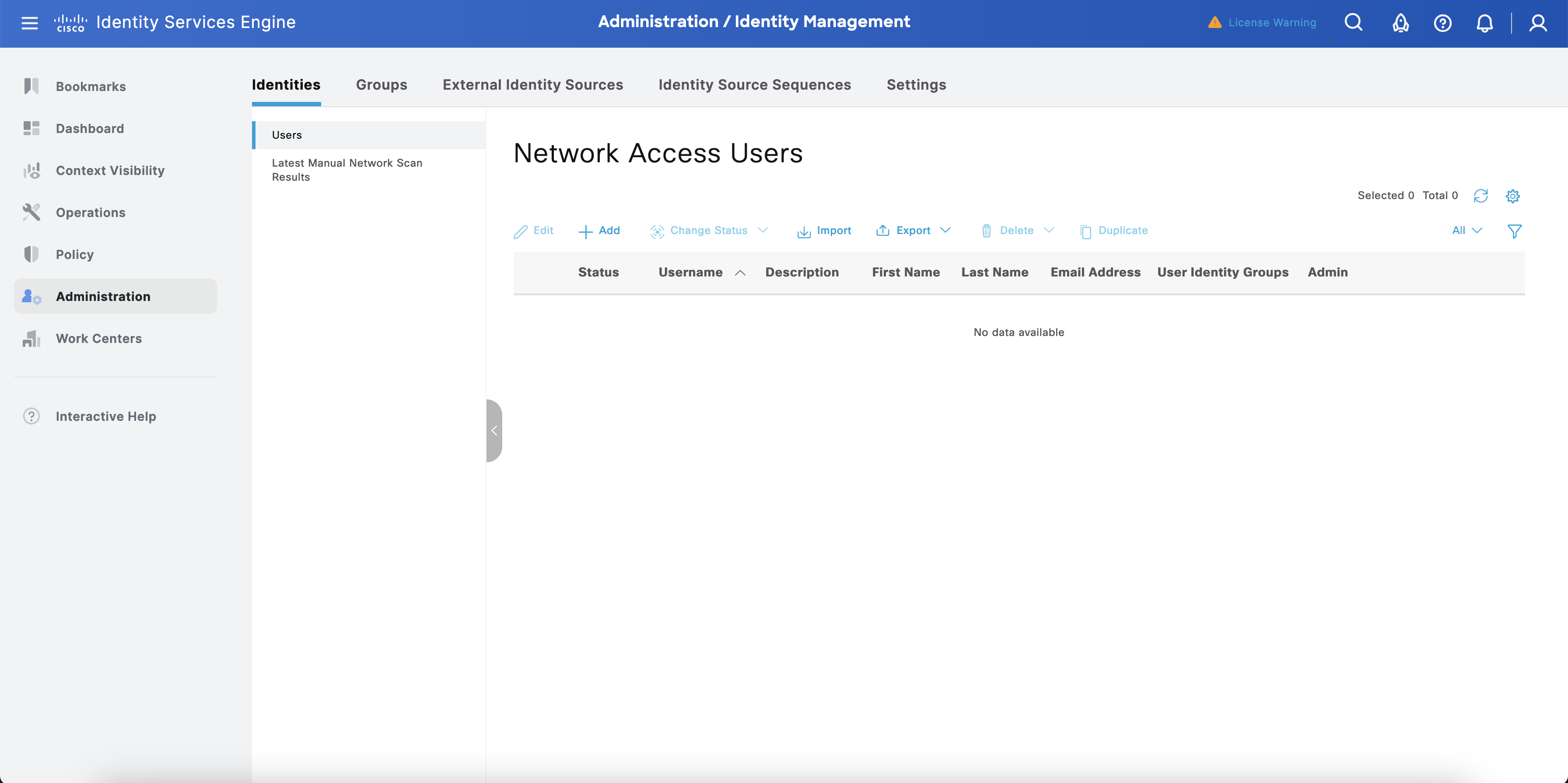
An ISE identity must be configured to represent an administrator. Create as many as needed.
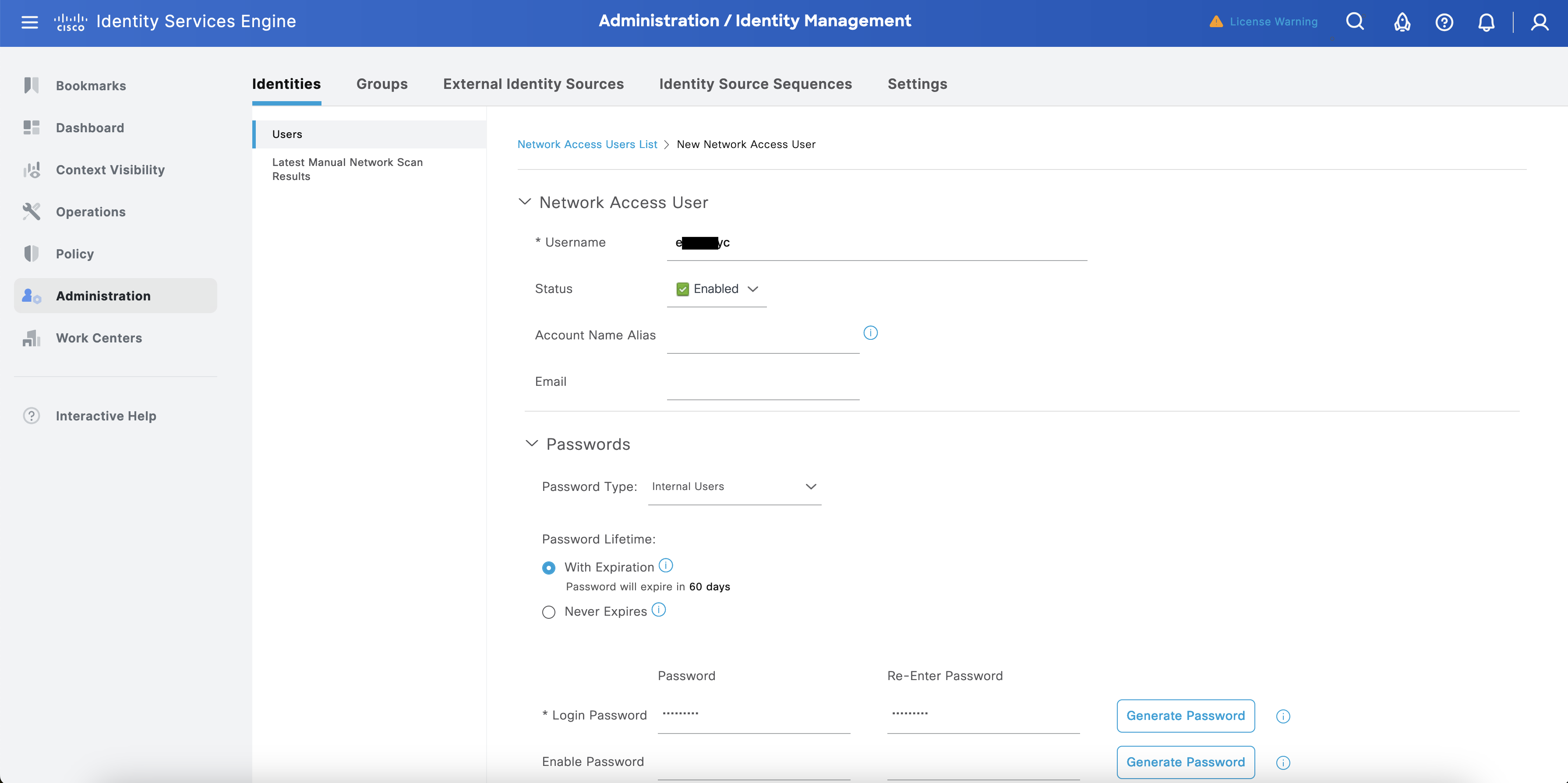
Navigate to Administration > Identity Management > Identities > Users.
Select + Add. Configure the fields Username, Login, and Password, then select Save
Configure a TACACS+ policy
In this phase, ISE is configured to return TACACS+ ACCESS_ACCEPT
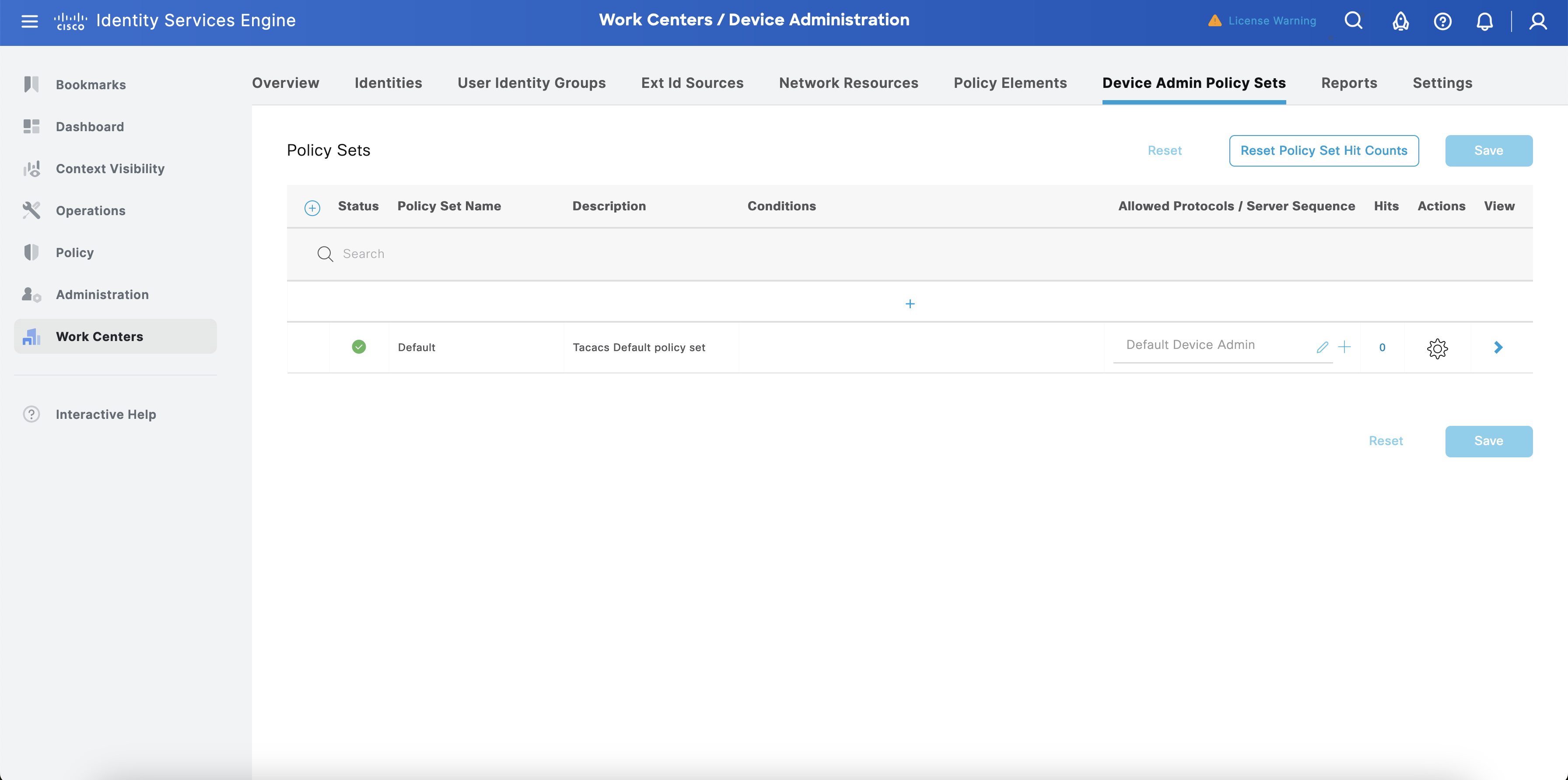
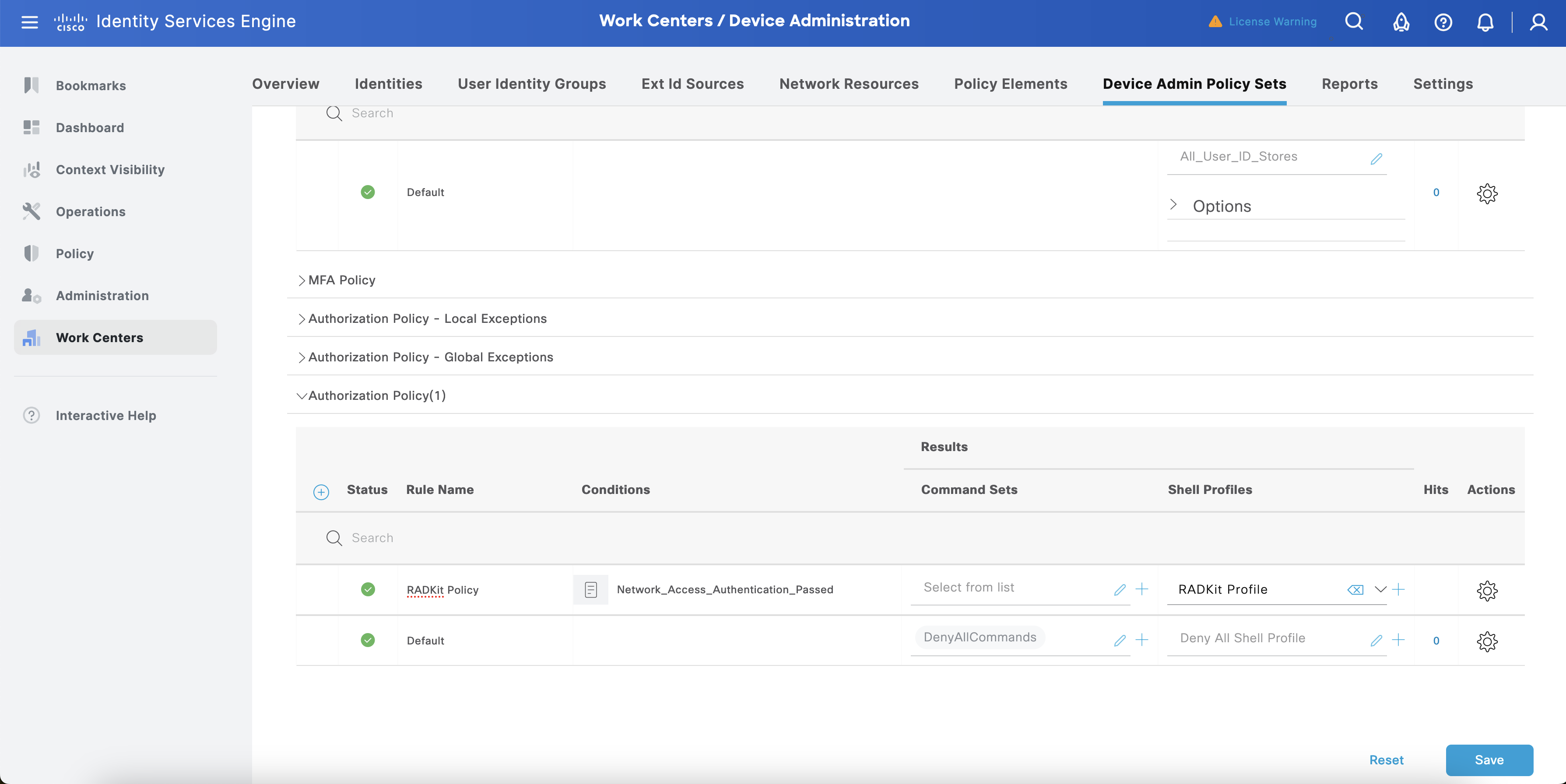
Navigate to Work Centers > Device Administration. Select > against Policy Set of your choice.
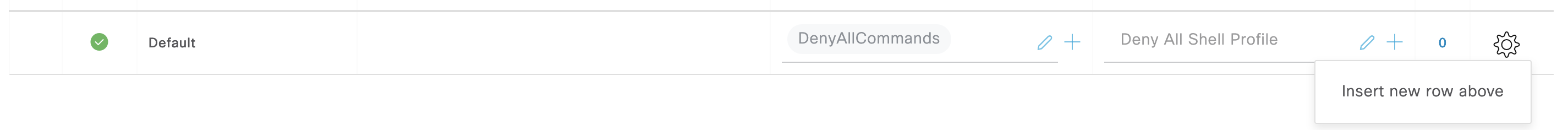
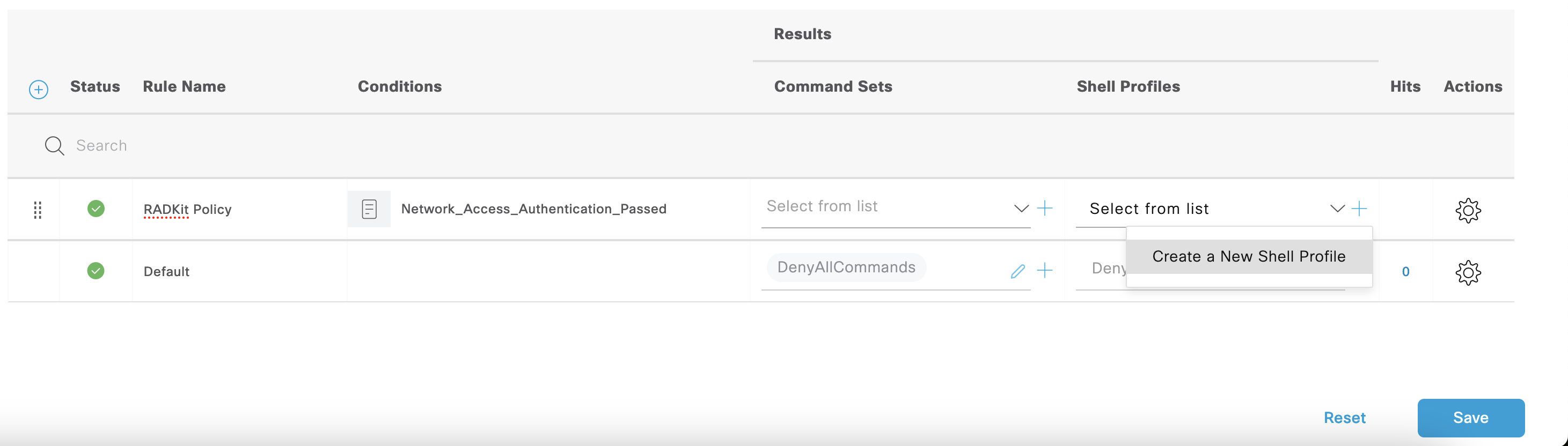
Scroll Down to the Authorization Policies and add New Authorization Policy by selecting Gear Icon and choosing Insert new role above.
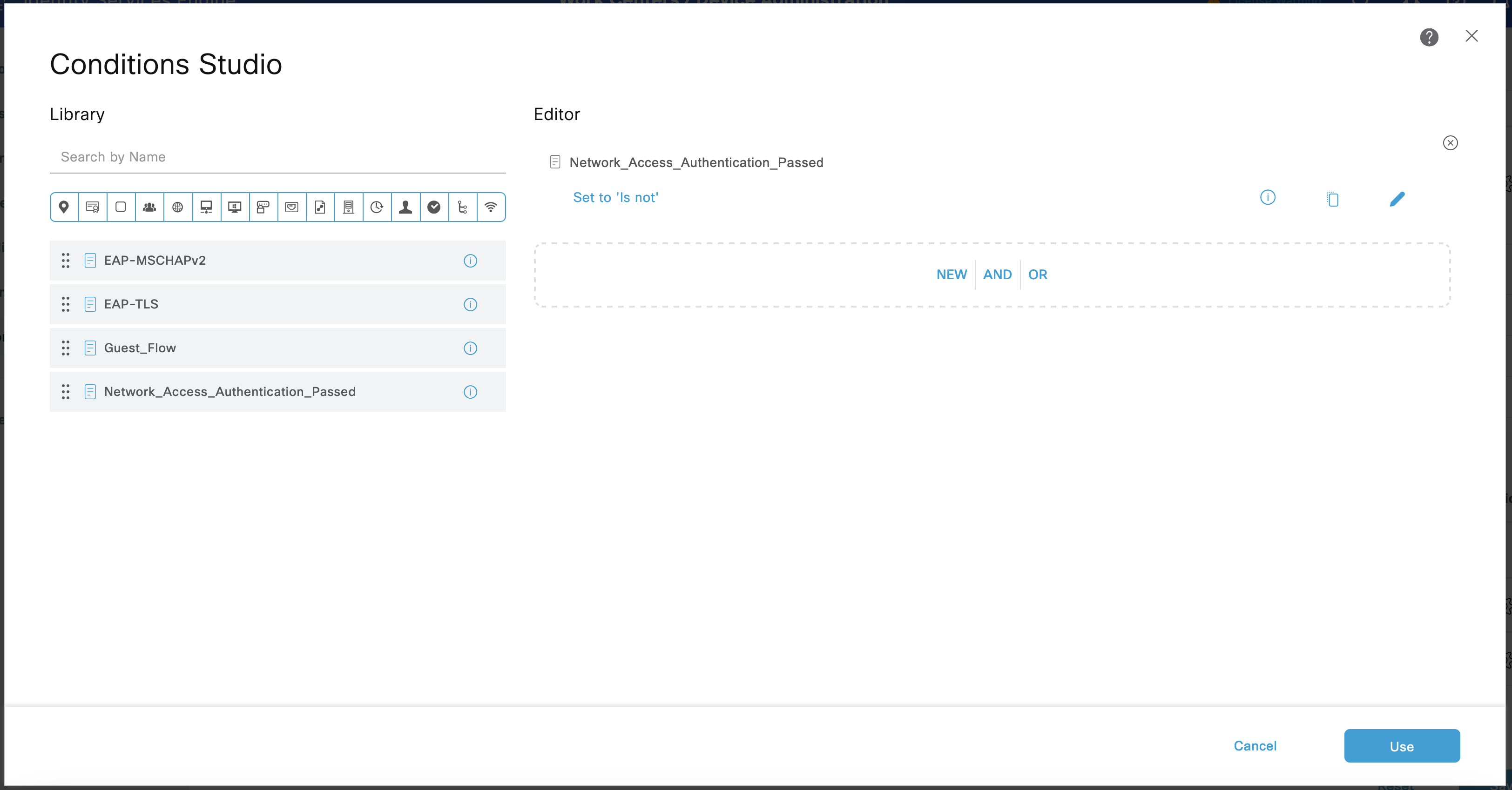
Select + in the Condition of the New policy to edit the condition. Drag and Drop Network_Access _Authentication_Passed from left screen to the Editor. Select Use.
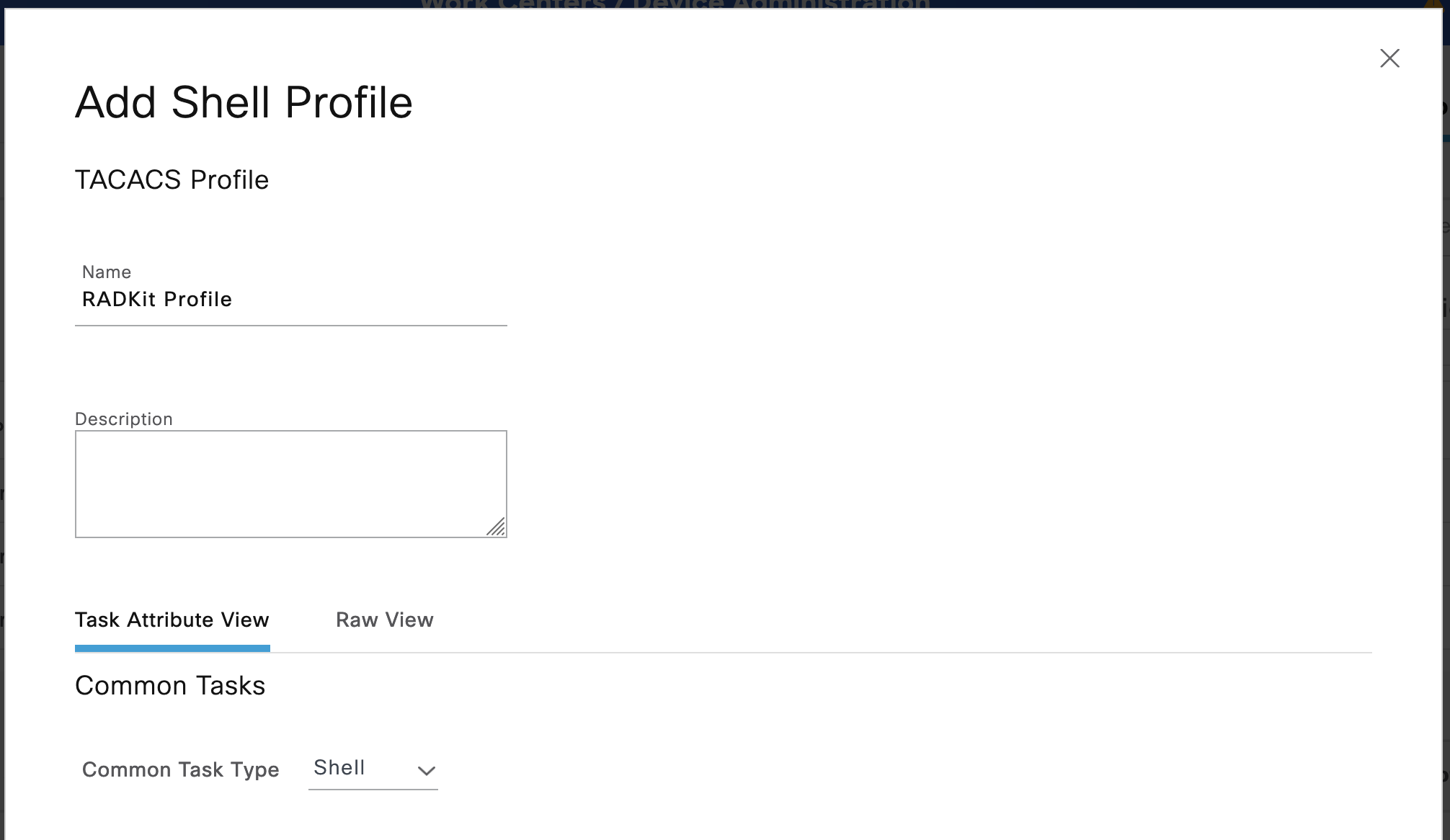
Under Shell Profile select +
Name the Shell Profile and click Save
Save the Policy
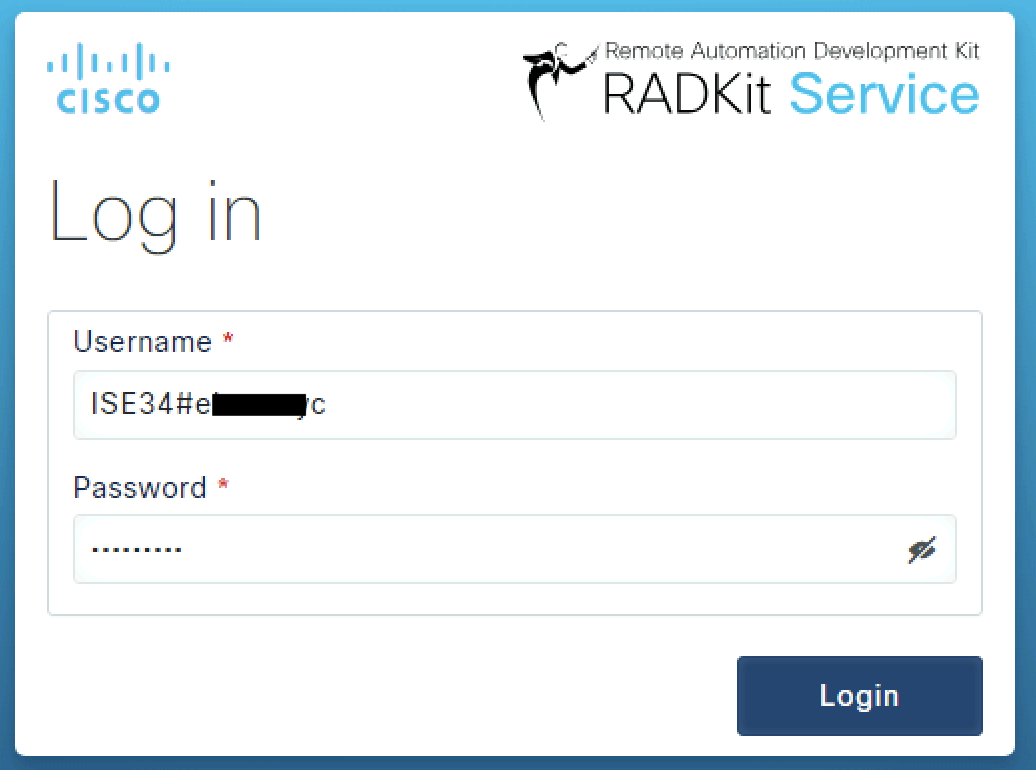
Login to RADKit with an ISE-bound administrator
In order to login to RADKit, use the format of <External TACACS+ Server>#<username>
Check ISE Live Logs
Verify Successful authentication on ISE
Navigate to Operations > TACACS > Live Logs, and confirm the RADKit was able to successfully authenticate the administrator with ISE.