External sources
The external sources feature enables integration with third-party applications and services. It allows for the delegation of device authentication and/or administrative authentication, such as external secret storage or third-party admin authentication methods.
There are two types of authentication:
Admin Authentication: used by RADKit Service to authenticate RADKit administrators (e.g at the RADKit WebUI logon).
Device Authentication: used by RADKit Service to authenticate to network devices.
The purpose of Admin external sources is to allow for the authentication of RADKit administrators to be delegated to the company credentials management system.
The purposes of Device external sources is to detach the credentials to a device from the main RADKit device definition. This separation allows for the credentials to be stored in
a secure location, such as a secrets management system (Vault, TACACS+ server, …), or
a central place, in the RADKit database in order to minimize the effort of updating all credentials at once.
Warning
Currently, the configuration of external sources is exclusively available through
the Service WebUI and is accessible solely to the superadmin user role. To manage
external sources, navigate to the External Sources tab where you can add, edit,
or remove configurations.
Admin authentication
When an administrator is defined on an external source, prefix the admin username with the
external source name and a hash symbol: <name_of_external_source>#<admin_user>.
As for now only TACACS+ and plugins are capable of admin authentication:
TACACS+
Plugin
Device authentication
Device authentication details are covered in Device Templates.
CyberArk CCP
Note
This section is a work in progress.
CyberArk Conjur
Note
This section is a work in progress.
Static Credentials
Note
This section is a work in progress.
Static credentials is useful when many devices share the same credentials. The device definition can refer to the external source of type Static Credentials, which stores the credentials in an encrypted form in the RADKit database.
When credentials need to be updated, only the Static Credentials definition needs to be updated, and all referring devices will automatically use the new credentials.
The statc credentials can be configured by referencing the external source in the YAML configuration:
terminal: !combine
- !external <name_of_external_source>
Static credentials external source also allows for secret retrieval, which can be specified in the YAML configuration as follows:
terminal:
password: !external <name_of_external_source>
username: !external <name_of_external_source>
Static Credentials Mapping
Static Credentials Mapping is a type of external source similar to Static Credentials, however in the case of mapping you can define a username/password pair for a specific remote user. In the remote user field you can use regexes, which means that the first field can be a specific email address for the user.
I.e.: user@cisco.com and the next one can be a wildcard .*.cisco.com.
The order determines the selection of the remote user credentials. If the previous regex match matches, the next ones are not checked.
terminal:
password: !external <name_of_external_source>
username: !external <name_of_external_source>
HashiCorp Vault
Integrating HashiCorp Vault with RADKit allows you to securely access your secrets.
Here is how you can get started:
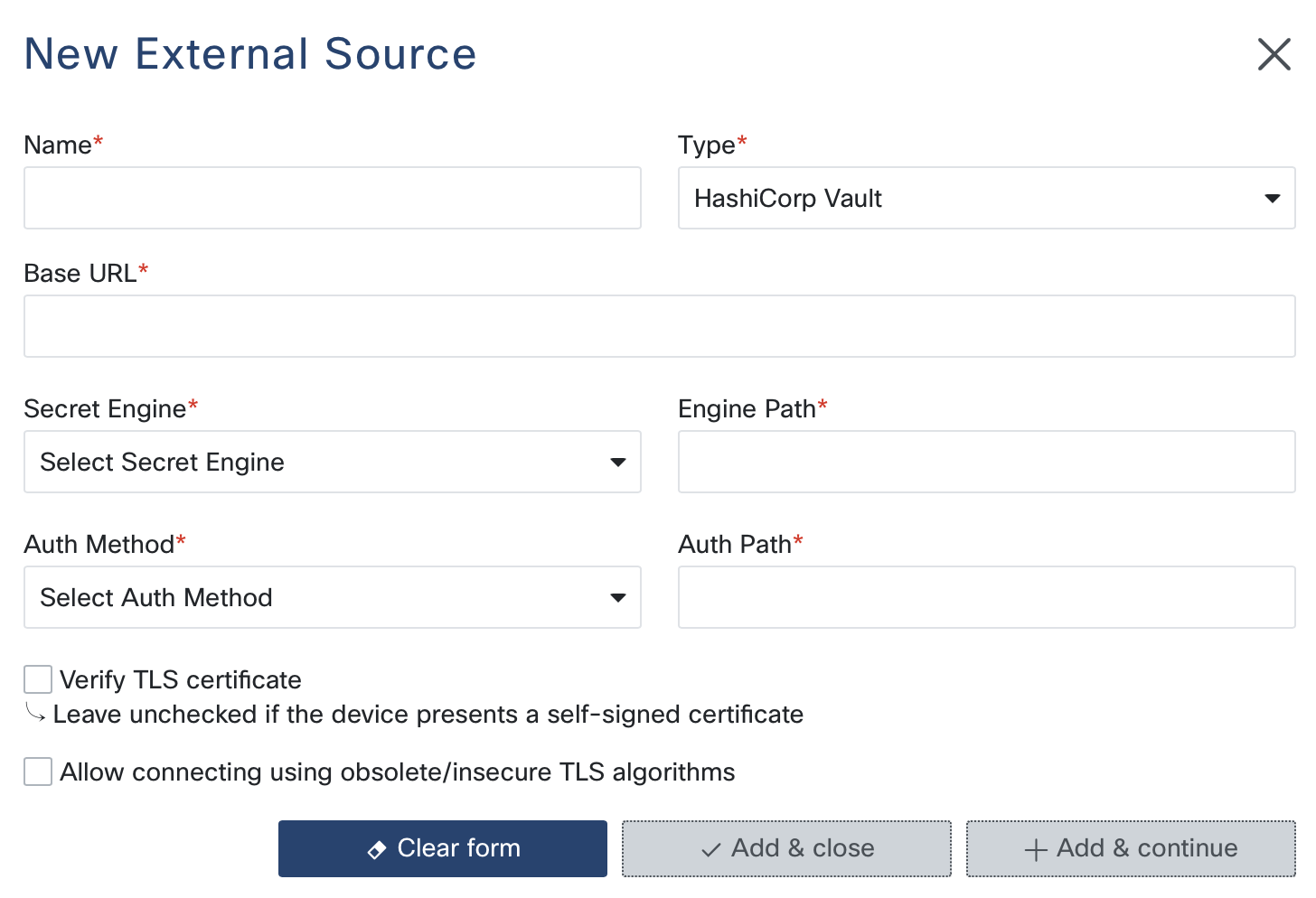
Configuration Steps
Base URL: Provide the base URL of your HashiCorp Vault server. This is the primary endpoint for API interactions. Ensure the URL is correct and accessible from your network.
Secret Engine: Select the secret engine type you want to use:
Cubbyhole: Used for storing secrets in a private, per-client space.
KV v1: The first version of HashiCorp Vault’s key-value store.
KV v2: An enhanced version of the key-value store with support for versioning.
Engine Path: Specify the path for the secret engine. This is the location within the Vault where your secrets are stored. Default paths are available based on the selected secret engine:
Cubbyhole: Defaults to /cubbyhole/
KV v1 and KV v2: Defaults to /secret/
Auth Method: Choose the authentication method for accessing Vault:
Token: Use a pre-generated token for authentication. This method is straightforward and requires a token with appropriate permissions.
AppRole: Use an AppRole to authenticate. This method involves providing a Role ID and a Secret ID.
Auth Path: Enter the path for authentication. This path is used to authenticate the client against the Vault server. Default paths are set based on the chosen authentication method:
Token: Defaults to /token/
AppRole: Defaults to /approle/
Token/Role ID/Secret ID:
If using Token authentication, provide the token value.
If using AppRole authentication, provide the Role ID and Secret ID.
Verify TLS Certificate: Check this option if you want to verify the Vault server’s TLS certificate. It’s recommended to enable this in production environments to ensure secure communication.
Use Insecure TLS Algorithms: Enable this option if your Vault server requires support for outdated or insecure TLS algorithms. Use this option with caution.
Note
Ensure that the Vault server is configured with the necessary policies and permissions to allow the RADKit Service to access the required secrets
Usage
To retrieve a specific secret from HashiCorp Vault, reference the external source by name in the YAML configuration, including the secret’s path:
terminal:
password: !external
name: <name_of_external_source>
values:
path: <secret_path/key>
Plugin
This external source type allows the integration of third-party external source implementations. Plugins are added by installing plugin packages that will be visible during the configuration.
Plugin package
Plugin packages are Python packages that uses metadata for plugins through entrypoints.
The plugin package needs to register classes as a entrypoints for radkit_service.external_sources.plugins group.
Examples:
pyproject.toml
[project.entry-points."radkit_service.external_sources.plugins"]
"My Custom Plugin" = "my_package.my_module:MyClass"
setup.py
from setuptools import setup
setup(
...,
entry_points={
"radkit_service.external_sources.plugins": [
"My Custom Plugin = my_package.my_module:MyClass",
],
},
)
config.cfg
[options.entry_points]
radkit_service.external_sources.plugins =
My Custom Plugin = my_package.my_module:MyClass
Protocol
To fulfill the protocol’s needs, the configured implementation must follow the defined protocol:
- class radkit_service.external_sources.ExternalSource
Bases:
ProtocolExternal Source Protocol definition.
There are four methods for utilizing external sources:
Generating terminal/netconf/snmp/swagger/http connection parameters:
In this method, within the YAML protocol definitions, the external source is cited in the protocol section, for example:
terminal: !external name: <name of referenced external source> values: <additional parameters for external source>
Here, the external source is tasked with constructing the
TerminalConnectionParametersdata structure, triggering the invocation ofcreate_terminal_connection_parameters.Retrieving secret attributes:
In this method, within the YAML protocol definitions, the external source is mentioned in the attribute definition, for instance:
terminal: password: !external name: <name of referenced external source> values: path: <secret path>
This indicates that the external source is accountable for procuring the specific secret, and
compute_device_parameterswill be executed as below:await external_source.compute_device_parameters(query=...)
Authenticating users:
In this method external source will be used for authenticating admins for login or authentication remote users for RPC calls. Passed username and password will be passed like this:
await external_source.authenticate_user( username=<username>, password=<password>, )
Authorizing users
In this method external source will be used for authorizing remote user for RPC calls.
Passed username will be passed like this:
await external_source.authorize_user(username=<username>)
Returned authorized user data structure is used downstream to accept or reject specific connection. If
Noneis returned, it means that user is not authorized.Note
As for now, we are unable to do direct SSO connections if external source is used for remote user authentication and authorization.
Should a particular external source implementation be incapable of generating connection parameters or retrieving secrets, it ought to return a
NotImplementedError.Warning
Implementing a cache mechanism might provide some performance improvements, but long TTLs can reduce reactivity for changes. For example, caching authentication results can lead to a situation where a non-authorized user might be authenticated due to the cache.
- async compute_device_parameters(
- query: ExternalSourceQuery,
- async authenticate_user(
- username: str,
- password: str,
Authenticates user by given credentials.
- async authorize_user(
- username: str,
Authorizes user.
Data types
- class radkit_service.external_sources.types.AuthenticatedUser
Bases:
TypedDictData structure used to describe authenticated user. Used in webserver session middleware.
- username: str
- email: str
- fullname: str
- description: str
- class radkit_service.external_sources.types.AuthorizedUser
Bases:
TypedDictData structure used to describe authorized user. Used in database device backend.
- connection_mode_cloud_active: bool
- connection_mode_direct_active: bool
- connection_mode_direct_sso_active: bool
- class radkit_common.types.ConnectionMethod
Bases:
str,Enum- SSH = 'SSH'
- SSHPUBKEY = 'SSHPUBKEY'
- TELNET = 'TELNET'
- TELNET_NO_AUTH = 'TELNET_NO_AUTH'
- NETCONF = 'NETCONF'